ETW概述
Event Tracing for Windows (ETW)是一种高效率的内核级跟踪工具,可以将内核或者应用程序定义的事件记录到日志文件中。使用者可以实时处理事件,也可以从日志文件中处理。
ETW可以动态地启用或禁用事件跟踪,无需重启计算机或应用程序。
Event Tracing API分为三个组件:
- Controllers,用于启动或停止事件跟踪会话(Event tracing session)和启用提供程序(providers)
- Providers,提供事件
- Consumers,消费事件
下图为事件跟踪模型
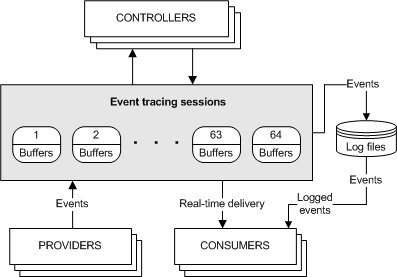
Controllers
Controllers用于定义日志文件的大小和位置,启动和停止事件跟踪会话以及启用提供程序,以便提供程序能将事件记录到会话,管理缓冲池的大小以及获取会话的执行统计信息。会话的统计信息包括缓冲区的使用数量,投递数量以及事件和缓冲区的丢失数量。
Providers
Providers具有提供事件的能力。在provider注册之后,controller就可以启用或禁用provider的事件跟踪。provider定义其对启用或禁用的解释。通常,一个启用的provider将生成事件,而禁用的provider则不会。这让使用者可以添加事件跟踪到应用程序中而无需一直生成事件。
尽管ETW模型将controller和provider分成了两个程序,但一个程序可以同时包含这两个组件
Providers有以下几种类型:
MOF (classic) providers:
- Use the RegisterTraceGuids and TraceEvent functions to register and write events.
- Use MOF classes to define events so that consumers know how to consume them.
- Can be enabled by only one trace session at a time.
WPP providers:
- Use the RegisterTraceGuids and TraceEvent functions to register and write events.
- Have associated TMF files (compiled into a binary’s .pdb) containing decoding information inferred from the preprocessor’s scan of WPP instrumentation in source code.
- Can be enabled by only one trace session at a time.
Manifest-based providers:
- Use EventRegister and EventWrite to register and write events.
- Use a manifest to define events so that consumers know how to consume them.
- Can be enabled by up to eight trace sessions simultaneously.
TraceLogging providers:
- Use TraceLoggingRegister and TraceLoggingWrite to register and write events.
- Use self-describing events so that the events themselves contain all required information for consuming them.
- Can be enabled by up to eight trace sessions simultaneously.
所有的providers都基于事件跟踪系列API (TraceEvent for legacy technologies and EventWrite/EventWriteEx for newer ones).
Consumers
Consumers可以选择一个或多个事件跟踪会话作为事件的源。consumer可以同时从多个事件跟踪会话中请求事件;系统按事件顺序投递事件。consumer可以从日志文件中接收事件,也可以从会话中实时接收事件。当处理事件时,consumer可以指定开始和结束时间,只有在指定时间内的事件才会被投递。
logman使用
列出所有正在运行的跟踪会话
1 | > logman query -ets |
列出所有订阅跟踪会话的提供者
1 | > logman query "EventLog-Application" -ets |
列出所有已注册的ETW提供者
1 | > logman query providers |
单独查看提供者
1 | > logman query providers Microsoft-Windows-PowerShell |
查看进程向哪些提供者写入事件
1 | > logman query providers -pid 5244 |
代码示例
NT Kernel Logger的开启与事件获取(TdhFormatProperty)
1 |
|