WFP简介
Windows Filtering Platform (WFP) 是用来创建网络过滤应用的一组API和系统服务,以代替以前的过滤技术比如Transport Driver Interface (TDI) filters,Network Driver Interface Specification (NDIS) filters,和Winsock Layered Service Providers (LSP)。
WFP框架结构
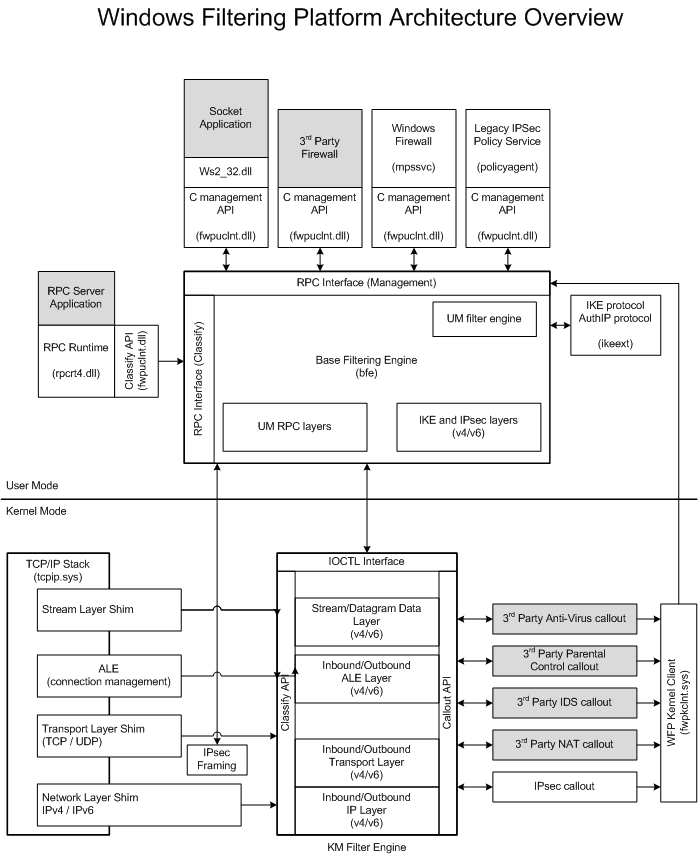
从图中可知WFP分为用户模式的Base Filtering Engine (BFE)和内核模式的KM Filter Engine。用户可以在用户层通过API与BFE交互,BFE再与KMFE交互,也可以再内核层直接与KMFE交互。
WFP运作方式
WFP通过以下四个部分执行任务:Layers, Filters, Shims and Callouts.
Layers
WFP过滤引擎分为多个层(Layers),对应系统网络协议栈的各个层,从中接受特定的数据。分层是一个容器,包含了各种过滤器。
Filters
过滤器是一组规则用来匹配传入和传出的网络数据包,并告诉过滤引擎对这些网络数据包进行什么操作,包括调用callout来进行深层次检查。
Shims
垫片(Shims)是一个内核模式组件,被安插在网络协议栈的不同层中,将网络数据分类到过滤引擎的不同分层,并让过滤引擎做出判断,最终也是垫片对这些网络数据执行对应操作。
Callouts
Callouts是驱动程序注册的一组接口,用来对网络数据包进行分析和处理。如果过滤器有指定callout,那么当过滤器匹配到对应的网络数据时便可以调用该接口。Callouts只能通过驱动注册,但可以在内核层和用户层中添加到过滤器,系统也内置了一些callouts。
WFP例子
比较重要的几个成员的文档介绍:
Filtering Conditions: https://docs.microsoft.com/en-us/windows/win32/fwp/filtering-conditions
Filtering Layer Identifiers: https://docs.microsoft.com/en-us/windows/win32/fwp/management-filtering-layer-identifiers-
用户层
通过FWPM_LAYER_ALE_RESOURCE_ASSIGNMENT_V4对指定程序在分配端口等资源的时候进行拦截。
1 |
|
内核层
还是通过FWPM_LAYER_ALE_RESOURCE_ASSIGNMENT_V4对指定端口进行拦截,但是是从callout处进行拦截,此处用的是最简单的功能,callout能做的事远不止如此。
1 |
|